In the fields of network operation and maintenance, troubleshooting, and security analysis, accurately and efficiently acquiring network data streams is the foundation for conducting various tasks. As two mainstream network data acquisition technologies, TAP (Test Access Point) and SPAN (Switched Port Analyzer, also commonly referred to as port mirroring) play important roles in different scenarios due to their distinct technical characteristics. A deep understanding of their features, advantages, limitations, and applicable scenarios is crucial for network engineers to formulate reasonable data collection plans and improve network management efficiency.
TAP: A Comprehensive and Visible "Lossless" Data Capture Solution
TAP is a hardware device operating at the physical or data link layer. Its core function is to achieve 100% replication and capture of network data streams without interfering with the original network traffic. By being connected in series in a network link (e.g., between a switch and a server, or a router and a switch), it replicates all upstream and downstream data packets passing through the link to a monitoring port using "optical splitting" or "traffic splitting" methods, for subsequent processing by analysis devices (such as network analyzers and Intrusion Detection Systems - IDS).
Core Features: Centered on "Integrity" and "Stability"
1. 100% Data Packet Capture with No Loss Risk
This is the most prominent advantage of TAP. Since TAP operates at the physical layer and directly replicates electrical or optical signals in the link, it does not rely on the switch's CPU resources for data packet forwarding or replication. Therefore, regardless of whether the network traffic is at its peak or contains large-sized data packets (such as Jumbo Frames with a large MTU value), all data packets can be completely captured without packet loss caused by insufficient switch resources. This "lossless capture" feature makes it the preferred solution for scenarios requiring accurate data support (such as fault root cause location and network performance baseline analysis).
2. No Impact on Original Network Performance
The working mode of TAP ensures that it does not cause any interference to the original network link. It neither modifies the content, source/destination addresses, or timing of data packets nor occupies the switch's port bandwidth, cache, or processing resources. Even if the TAP device itself malfunctions (such as power failure or hardware damage), it will only result in no data output from the monitoring port, while the communication of the original network link remains normal, avoiding the risk of network interruption caused by the failure of data collection devices.
3. Support for Full-Duplex Links and Complex Network Environments
Modern networks mostly adopt the full-duplex communication mode (i.e., upstream and downstream data can be transmitted simultaneously). TAP can capture data streams in both directions of a full-duplex link and output them through independent monitoring ports, ensuring that the analysis device can fully restore the two-way communication process. In addition, TAP supports various network rates (such as 100M, 1G, 10G, 40G, and even 100G) and media types (twisted pair, single-mode fiber, multi-mode fiber), and can be adapted to network environments of different complexities such as data centers, core backbone networks, and campus networks.
Application Scenarios: Focusing on "Accurate Analysis" and "Key Link Monitoring"
1. Network Troubleshooting and Root Cause Location
When problems such as packet loss, delay, jitter, or application lag occur in the network, it is necessary to restore the scenario when the fault occurred through a complete data packet stream. For example, if an enterprise's core business systems (such as ERP and CRM) experience intermittent access timeouts, operation and maintenance personnel can deploy a TAP between the server and the core switch to capture all round-trip data packets, analyze whether there are issues such as TCP retransmission, packet loss, DNS resolution delay, or application-layer protocol errors, and thereby quickly locate the root cause of the fault (such as link quality problems, slow server response, or middleware configuration errors).
2. Network Performance Baseline Establishment and Anomaly Monitoring
In network operation and maintenance, establishing a performance baseline under normal business loads (such as average bandwidth utilization, data packet forwarding delay, and TCP connection establishment success rate) is the basis for monitoring anomalies. TAP can stably capture full-volume data of key links (such as between core switches and between egress routers and ISPs) for a long time, helping operation and maintenance personnel count various performance indicators and establish an accurate baseline model. When subsequent anomalies such as sudden traffic surges, abnormal delays, or protocol anomalies (such as abnormal ARP requests and a large number of ICMP packets) occur, anomalies can be quickly detected by comparing with the baseline, and timely intervention can be carried out.
3. Compliance Auditing and Threat Detection with High Security Requirements
For industries with high requirements for data security and compliance such as finance, government affairs, and energy, it is necessary to conduct full-process auditing of the transmission process of sensitive data or accurately detect potential network threats (such as APT attacks, data leakage, and malicious code propagation). The lossless capture feature of TAP ensures the integrity and accuracy of audit data, which can meet the requirements of laws and regulations such as the "Network Security Law" and "Data Security Law" for data retention and auditing; at the same time, full-volume data packets also provide rich analysis samples for threat detection systems (such as IDS/IPS and sandbox devices), helping to detect low-frequency and hidden threats hidden in normal traffic (such as malicious code in encrypted traffic and penetration attacks disguised as normal business).
Limitations: Trade-off between Cost and Deployment Flexibility
The main limitations of TAP lie in its high hardware cost and low deployment flexibility. On the one hand, TAP is a dedicated hardware device, and in particular, TAPs supporting high rates (such as 40G and 100G) or optical fiber media are much more expensive than the software-based SPAN function; on the other hand, TAP needs to be connected in series in the original network link, and the link needs to be temporarily interrupted during deployment (such as plugging and unplugging network cables or optical fibers). For some core links that do not allow interruption (such as financial transaction links operating 24/7), deployment is difficult, and TAP access points usually need to be reserved in advance during the network planning phase.
SPAN: A Cost-Effective and Flexible "Multi-Port" Data Aggregation Solution
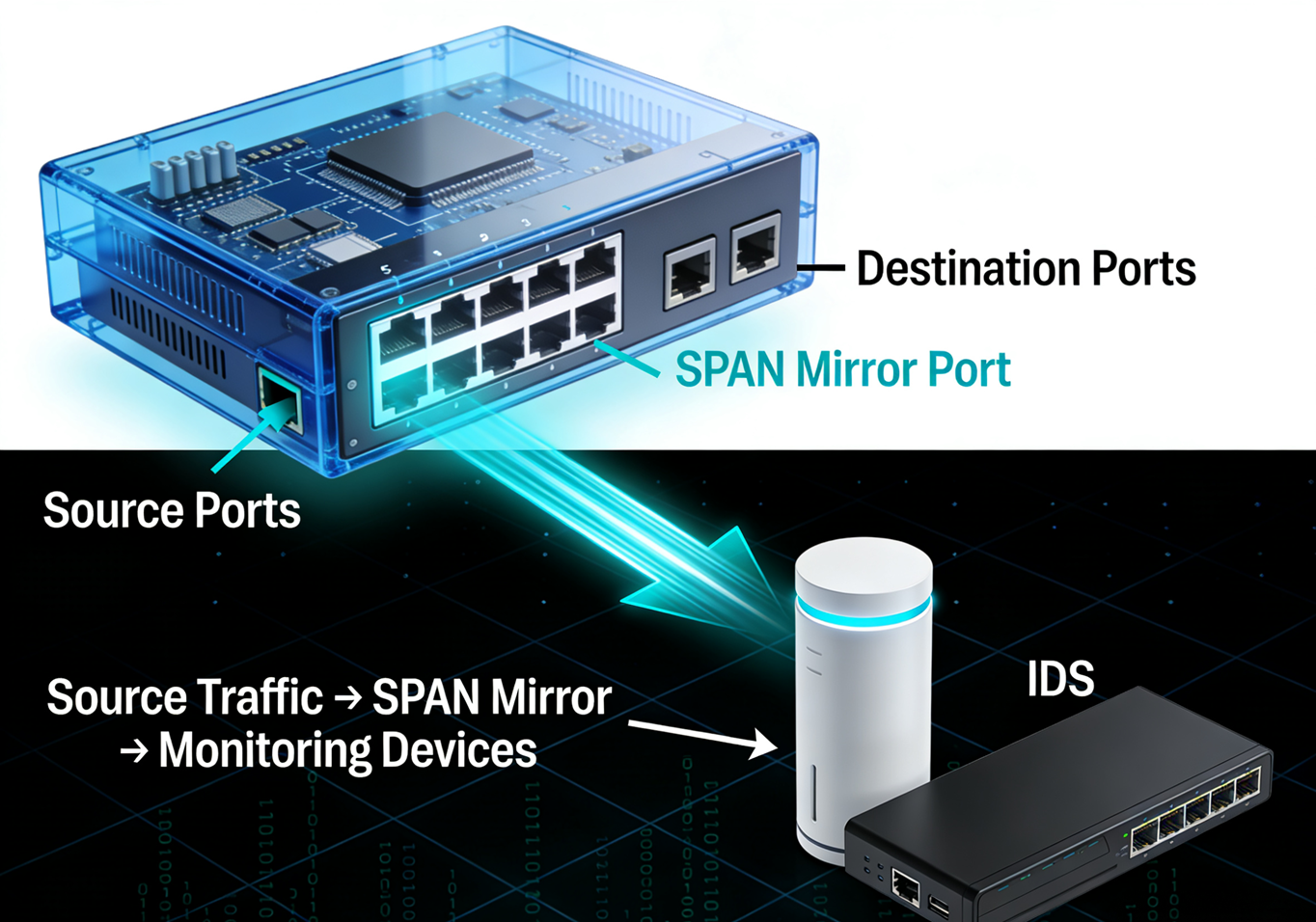
SPAN is a software function built into switches (some high-end routers also support it). Its principle is to configure the switch internally to replicate traffic from one or more source ports (Source Ports) or source VLANs to a designated monitoring port (Destination Port, also known as a mirror port) for reception and processing by the analysis device. Unlike TAP, SPAN does not require additional hardware devices and can realize data collection only by relying on the software configuration of the switch.
Core Features: Centered on "Cost-Effectiveness" and "Flexibility"
1. Zero Additional Hardware Cost and Convenient Deployment
Since SPAN is a function built into the switch firmware, there is no need to purchase dedicated hardware devices. Data collection can be quickly enabled only by configuring through the CLI (Command Line Interface) or Web management interface (such as specifying the source port, monitoring port, and mirroring direction (inbound, outbound, or bidirectional)). This "zero hardware cost" feature makes it an ideal choice for scenarios with limited budgets or temporary monitoring needs (such as short-term application testing and temporary troubleshooting).
2. Support for Multi-Source Port / Multi-VLAN Traffic Aggregation
A major advantage of SPAN is that it can replicate traffic from multiple source ports (such as user ports of multiple access-layer switches) or multiple VLANs to the same monitoring port at the same time. For example, if enterprise operation and maintenance personnel need to monitor the traffic of employee terminals in multiple departments (corresponding to different VLANs) accessing the Internet, there is no need to deploy separate collection devices at the egress of each VLAN. By aggregating the traffic of these VLANs to one monitoring port through SPAN, centralized analysis can be realized, greatly improving the flexibility and efficiency of data collection.
3. No Need to Interrupt the Original Network Link
Different from the series deployment of TAP, both the source port and the monitoring port of SPAN are ordinary ports of the switch. During the configuration process, there is no need to plug and unplug the network cables of the original link, and there is no impact on the transmission of the original traffic. Even if it is necessary to adjust the source port or disable the SPAN function later, it can be done only by modifying the configuration through the command line, which is convenient to operate and has no interference with network services.
Application Scenarios: Focusing on "Low-Cost Monitoring" and "Centralized Analysis"
1. User Behavior Monitoring in Campus Networks / Enterprise Networks
In campus networks or enterprise networks, administrators often need to monitor whether employee terminals have illegal access (such as accessing illegal websites and downloading pirated software) and whether there are a large number of P2P downloads or video streams occupying bandwidth. By aggregating the traffic of user ports of access-layer switches to the monitoring port through SPAN, combined with traffic analysis software (such as Wireshark and NetFlow Analyzer), real-time monitoring of user behavior and statistics of bandwidth occupation can be realized without additional hardware investment.
2. Temporary Troubleshooting and Short-Term Application Testing
When temporary and occasional faults occur in the network, or when it is necessary to conduct traffic testing on a newly deployed application (such as an internal OA system and a video conferencing system), SPAN can be used to quickly build a data collection environment. For example, if a department reports frequent freezes in video conferences, operation and maintenance personnel can temporarily configure SPAN to mirror the traffic of the port where the video conference server is located to the monitoring port. By analyzing the data packet delay, packet loss rate, and bandwidth occupation, it can be determined whether the fault is caused by insufficient network bandwidth or data packet loss. After the troubleshooting is completed, the SPAN configuration can be disabled without affecting subsequent network operations.
3. Traffic Statistics and Simple Auditing in Small and Medium-Sized Networks
For small and medium-sized networks (such as small enterprises and campus laboratories), if the requirement for data collection integrity is not high, and only simple traffic statistics (such as bandwidth utilization of each port and traffic proportion of Top N applications) or basic compliance auditing (such as recording the website domain names accessed by users) are needed, SPAN can fully meet the needs. Its low-cost and easy-to-deploy features make it a cost-effective choice for such scenarios.
Limitations: Shortcomings in Data Integrity and Performance Impact
1. Risk of Data Packet Loss and Incomplete Capture
The replication of data packets by SPAN relies on the CPU and cache resources of the switch. When the traffic of the source port is at its peak (such as exceeding the switch's cache capacity) or the switch is processing a large number of forwarding tasks at the same time, the CPU will give priority to ensuring the forwarding of the original traffic, and reduce or suspend the replication of SPAN traffic, resulting in packet loss at the monitoring port. In addition, some switches have restrictions on the mirroring ratio of SPAN (such as only supporting the replication of 80% of the traffic) or do not support the complete replication of large-sized data packets (such as Jumbo Frames). All these will lead to incomplete collected data and affect the accuracy of subsequent analysis results.
2. Occupying Switch Resources and Potential Impact on Network Performance
Although SPAN does not directly interrupt the original link, when the number of source ports is large or the traffic is heavy, the data packet replication process will occupy the CPU resources and internal bandwidth of the switch. For example, if the traffic of multiple 10G ports is mirrored to a 10G monitoring port, when the total traffic of the source ports exceeds 10G, not only will the monitoring port suffer from packet loss due to insufficient bandwidth, but the CPU utilization of the switch may also increase significantly, thereby affecting the data packet forwarding efficiency of other ports and even causing a decline in the overall performance of the switch.
3. Function Dependence on Switch Model and Limited Compatibility
The level of support for the SPAN function varies greatly among switches of different manufacturers and models. For example, low-end switches may only support a single monitoring port and do not support VLAN mirroring or full-duplex traffic mirroring; the SPAN function of some switches has a "one-way mirroring" restriction (i.e., only mirroring inbound or outbound traffic, and cannot mirror bidirectional traffic at the same time); in addition, cross-switch SPAN (such as mirroring the port traffic of switch A to the monitoring port of switch B) needs to rely on specific protocols (such as Cisco's RSPAN and Huawei's ERSPAN), which has complex configuration and low compatibility, and is difficult to adapt to the environment of mixed networking of multiple manufacturers.
Core Difference Comparison and Selection Suggestions between TAP and SPAN
Core Difference Comparison
To more clearly show the differences between the two, we compare them from the dimensions of technical characteristics, performance impact, cost, and applicable scenarios:
|
Comparison Dimension
|
TAP (Test Access Point)
|
SPAN (Switched Port Analyzer)
|
|
Data Capture Integrity
|
100% lossless capture, no loss risk
|
Relies on switch resources, prone to packet loss at high traffic, incomplete capture
|
|
Impact on Original Network
|
No interference, fault does not affect the original link
|
Occupies switch CPU/bandwidth at high traffic, may cause network performance degradation
|
|
Hardware Cost
|
Requires purchase of dedicated hardware, high cost
|
Built-in switch function, zero additional hardware cost
|
|
Deployment Flexibility
|
Needs to be connected in series in the link, network interruption required for deployment, low flexibility
|
Software configuration, no network interruption required, supports multi-source aggregation, high flexibility
|
|
Applicable Scenarios
|
Core links, accurate fault location, high-security auditing, high-rate networks
|
Temporary monitoring, user behavior analysis, small and medium-sized networks, low-cost needs
|
|
Compatibility
|
Supports multiple rates/media, independent of switch model
|
Depends on switch manufacturer/model, large differences in function support, complex cross-device configuration
|
Selection Suggestions: "Accurate Matching" Based on Scenario Requirements
1. Scenarios Where TAP is Preferred
○ Monitoring of core business links (such as data center core switches and egress router links), requiring ensuring the integrity of data capture;
○ Network fault root cause location (such as TCP retransmission and application lag), requiring accurate analysis based on full-volume data packets;
○ Industries with high security and compliance requirements (finance, government affairs, energy), requiring meeting the integrity and non-tampering of audit data;
○ High-rate network environments (10G and above) or scenarios with large-sized data packets, requiring avoiding packet loss in SPAN.
2. Scenarios Where SPAN is Preferred
○ Small and medium-sized networks with limited budgets, or scenarios only requiring simple traffic statistics (such as bandwidth occupation and Top applications);
○ Temporary troubleshooting or short-term application testing (such as new system launch testing), requiring rapid deployment without long-term resource occupation;
○ Centralized monitoring of multi-source ports/multi-VLANs (such as campus network user behavior monitoring), requiring flexible traffic aggregation;
○ Monitoring of non-core links (such as user ports of access-layer switches), with low requirements for data capture integrity.
3. Hybrid Usage Scenarios
In some complex network environments, a hybrid deployment method of "TAP + SPAN" can also be adopted. For example, deploy TAP in the core links of the data center to ensure full-volume data capture for troubleshooting and security auditing; configure SPAN in access-layer or aggregation-layer switches to aggregate scattered user traffic for behavior analysis and bandwidth statistics. This not only meets the accurate monitoring needs of key links but also reduces the overall deployment cost.
So, as two core technologies for network data acquisition, TAP and SPAN have no absolute "advantages or disadvantages" but only "differences in scenario adaptation". TAP is centered on "lossless capture" and "stable reliability", and is suitable for key scenarios with high requirements for data integrity and network stability, but has high cost and low deployment flexibility; SPAN has the advantages of "zero cost" and "flexibility and convenience", and is suitable for low-cost, temporary, or non-core scenarios, but has the risks of data loss and performance impact.
In actual network operation and maintenance, network engineers need to select the most suitable technical solution based on their own business needs (such as whether it is a core link and whether accurate analysis is required), budget costs, network scale, and compliance requirements. At the same time, with the improvement of network rates (such as 25G, 100G, and 400G) and the upgrading of network security requirements, TAP technology is also constantly developing (such as supporting intelligent traffic splitting and multi-port aggregation), and switch manufacturers are also continuously optimizing the SPAN function (such as improving cache capacity and supporting lossless mirroring). In the future, the two technologies will further play their roles in their respective fields and provide more efficient and accurate data support for network management.
Post time: Dec-08-2025