In the era of cloud computing and network virtualization, VXLAN (Virtual Extensible LAN) has become a cornerstone technology for building scalable, flexible overlay networks. At the heart of VXLAN architecture lies the VTEP (VXLAN Tunnel Endpoint), a critical component that enables the seamless transmission of layer 2 traffic across layer 3 networks. As network traffic grows increasingly complex with various encapsulation protocols, the role of Network Packet Brokers (NPBs) with Tunnel Encapsulation Stripping capabilities has become indispensable in optimizing VTEP operations. This blog explores the fundamentals of VTEP and its relationship with VXLAN, then delves into how NPBs' tunnel encapsulation stripping function enhances VTEP performance and network visibility.
Understanding VTEP and Its Relationship with VXLAN
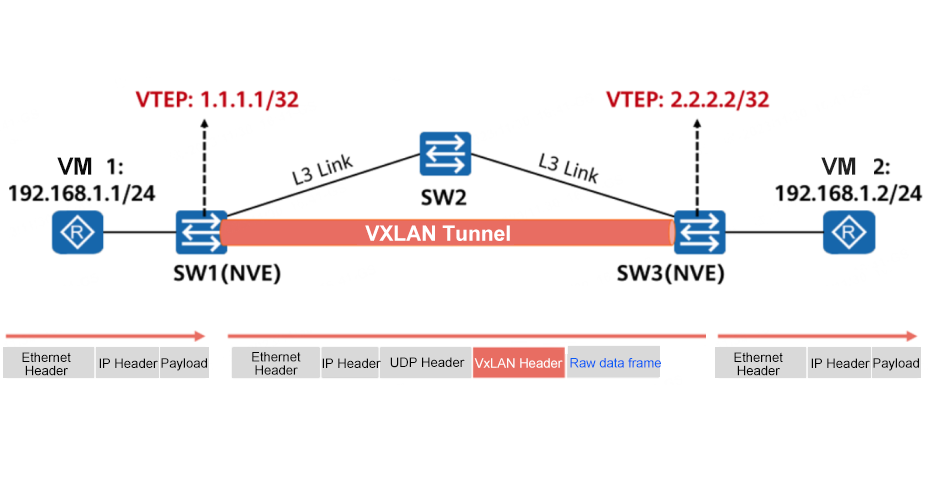
First, let's clarify the core concepts: VTEP, short for VXLAN Tunnel Endpoint, is a network entity responsible for encapsulating and decapsulating VXLAN packets in a VXLAN overlay network. It serves as the start and end point of VXLAN tunnels, acting as a "gateway" that bridges the virtual overlay network and the physical underlay network. VTEPs can be implemented as physical devices (such as VXLAN-capable switches or routers) or software entities (like virtual switches, container hosts, or proxies on virtual machines).
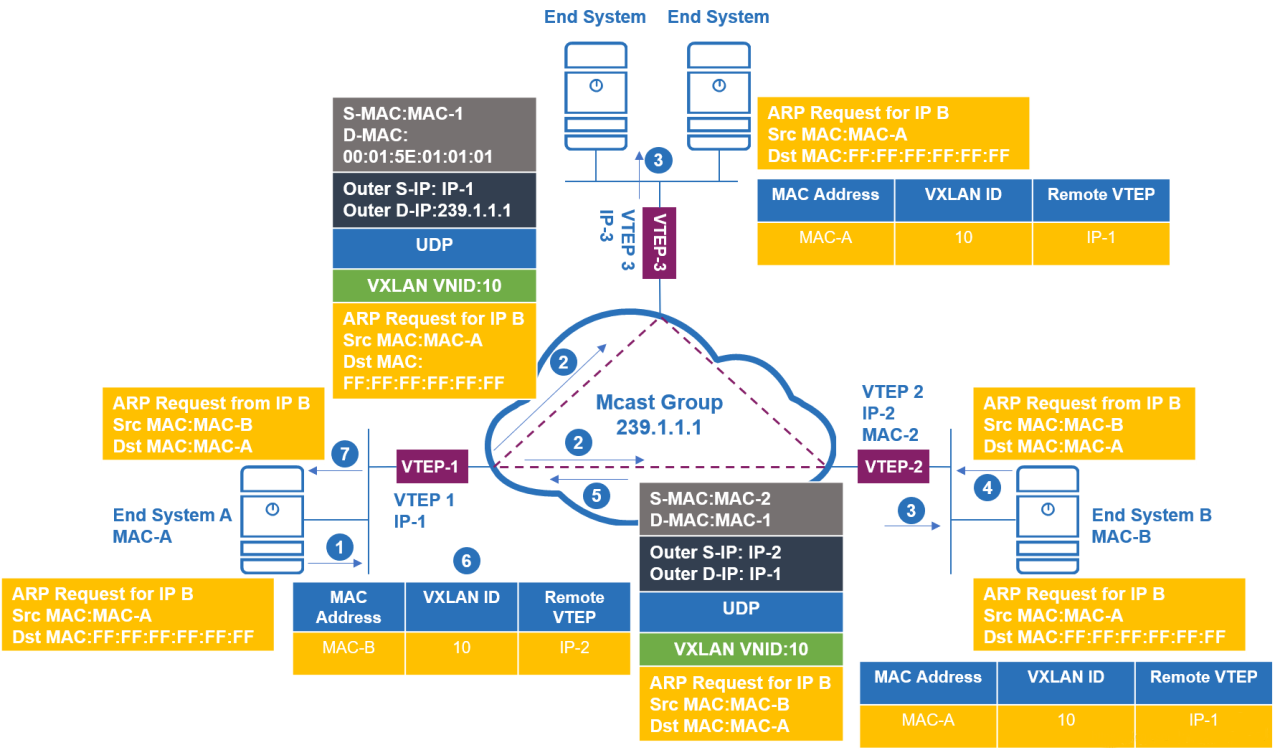
The relationship between VTEP and VXLAN is inherently symbiotic—VXLAN relies on VTEPs to realize its core functionality, while VTEPs exist exclusively to support VXLAN operations. VXLAN's core value is to create a virtual layer 2 network on top of a layer 3 IP network through MAC-in-UDP encapsulation, overcoming the scalability limitations of traditional VLANs (which only support 4096 VLAN IDs) with a 24-bit VXLAN Network Identifier (VNI) that enables up to 16 million virtual networks. Here's how VTEPs enable this: When a virtual machine (VM) sends traffic, the local VTEP encapsulates the original layer 2 Ethernet frame by adding a VXLAN header (containing the VNI), a UDP header (using port 4789 by default), an outer IP header (with the source VTEP IP and destination VTEP IP), and an outer Ethernet header. The encapsulated packet is then transmitted over the layer 3 underlay network to the destination VTEP, which decapsulates the packet by stripping off all outer headers, recovers the original Ethernet frame, and forwards it to the target VM based on the VNI.
Additionally, VTEPs handle critical tasks such as MAC address learning (dynamically mapping MAC addresses of local and remote hosts to VTEP IPs) and processing of Broadcast, Unknown Unicast, and Multicast (BUM) traffic—either through multicast groups or head-end replication in unicast-only mode. In essence, VTEPs are the building blocks that make VXLAN's network virtualization and multi-tenant isolation possible.
The Challenge of Encapsulated Traffic for VTEPs
In modern data center environments, VTEP traffic is rarely limited to pure VXLAN encapsulation. Traffic passing through VTEPs often carries multiple layers of encapsulation headers, including VLAN, GRE, GTP, MPLS, or IPIP, in addition to VXLAN. This encapsulation complexity poses significant challenges for VTEP operations and subsequent network monitoring, analysis, and security enforcement:
○ - Reduced Visibility: Most network monitoring and security tools (such as IDS/IPS, flow analyzers, and packet sniffers) are designed to process native layer 2/layer 3 traffic. Encapsulated headers obscure the original payload, making it impossible for these tools to accurately analyze traffic content or detect anomalies.
○ - Increased Processing Overhead: VTEPs themselves must spend additional computing resources to process multi-layer encapsulated packets, especially in high-traffic environments. This can lead to increased latency, reduced throughput, and potential performance bottlenecks.
○ - Interoperability Issues: Different network segments or multi-vendor environments may use different encapsulation protocols. Without proper header stripping, traffic may fail to be correctly forwarded or processed when passing through VTEPs, leading to interoperability problems.
How NPBs' Tunnel Encapsulation Stripping Empowers VTEPs
Mylinking™ Network Packet Brokers (NPBs) with Tunnel Encapsulation Stripping capabilities address these challenges by acting as a "Traffic pre-processor" for VTEPs. NPBs can strip various encapsulation headers (including VXLAN, VLAN, GRE, GTP, MPLS, and IPIP) from original data packets before forwarding the traffic to VTEPs or monitoring/security tools. This functionality delivers three key benefits for VTEP operations:
1. Enhanced Network Visibility and Security
By stripping encapsulation headers, NPBs expose the original payload of packets, enabling monitoring and security tools to "see" the actual traffic content. For example, when VTEP traffic is forwarded to an IDS/IPS, the NPB first strips off VXLAN and MPLS headers, allowing the IDS/IPS to detect malicious activity (such as malware or unauthorized access attempts) in the original frame. This is particularly critical in multi-tenant environments where VTEPs handle traffic from multiple tenants—NPBs ensure that security tools can inspect tenant-specific traffic without being hindered by encapsulation.
Moreover, NPBs can selectively strip headers based on traffic types or VNI, providing granular visibility into specific virtual networks. This helps network administrators troubleshoot issues (such as packet loss or latency) by enabling precise analysis of traffic within individual VXLAN segments.
2. Optimized VTEP Performance
NPBs offload the header stripping task from VTEPs, reducing the processing overhead on VTEP devices. Instead of VTEPs spending CPU resources on stripping multiple layers of headers (e.g., VLAN + GRE + VXLAN), NPBs handle this pre-processing step, allowing VTEPs to focus on their core responsibilities: encapsulation/decapsulation of VXLAN packets and tunnel management. This results in lower latency, higher throughput, and improved overall performance of the VXLAN overlay network—especially in high-density virtualization environments with thousands of VMs and heavy traffic loads.
For example, in a data center with NPBs and Switches acting as VTEPs, an NPB (such as Mylinking™ Network Packet Brokers) can strip VLAN and MPLS headers from incoming traffic before it reaches the VTEPs. This reduces the number of header processing operations the VTEPs need to perform, enabling them to handle more concurrent tunnels and traffic flows.
3. Improved Interoperability Across Heterogeneous Networks
In multi-vendor or multi-segment networks, different parts of the infrastructure may use different encapsulation protocols. For instance, traffic from a remote data center may arrive at a local VTEP with GRE encapsulation, while local traffic uses VXLAN. An NPB can strip these diverse headers (GRE, VXLAN, IPIP, etc.) and forward a consistent, native traffic stream to the VTEP, eliminating interoperability issues. This is particularly valuable in hybrid cloud environments, where traffic from public cloud services (often using GTP or IPIP encapsulation) needs to integrate with on-premises VXLAN networks via VTEPs.
Additionally, NPBs can forward the stripped headers as metadata to monitoring tools, ensuring that administrators retain context about the original encapsulation (such as VNI or MPLS label) while still enabling analysis of the native payload. This balance between header stripping and context preservation is key to effective network management.
How to implement the tunnel package stripping function in VTEP?
Tunnel encapsulation stripping in VTEP can be implemented through hardware-level configuration, software-defined policies, and synergy with SDN controllers, with core logic focusing on identifying tunnel headers → executing stripping actions → forwarding original payloads. The specific implementation methods vary slightly based on VTEP types (physical/software), and key approaches are as follows:
Now, we are talking about Implementation on Physical VTEPs (e.g., Mylinking™ VXLAN-capable Network Packet Brokers) here.
Physical VTEPs (such as Mylinking™ VXLAN-capable Network Packet Brokers) rely on hardware chips and dedicated configuration commands to achieve efficient encapsulation stripping, suitable for high-traffic data center scenarios:
Interface-based encapsulation matching: Create sub-interfaces on the physical access ports of VTEPs and configure encapsulation types to match and strip specific tunnel headers. For example, on Mylinking™ VXLAN-capable Network Packet Brokers, configure Layer 2 sub-interfaces to recognize 802.1Q VLAN tags or untagged frames, and strip VLAN headers before forwarding traffic to the VXLAN tunnel. For GRE/MPLS-encapsulated traffic, enable corresponding protocol parsing on the sub-interface to strip outer headers.
Policy-based header stripping: Use ACL (Access Control List) or traffic policy to define matching rules (e.g., matching UDP port 4789 for VXLAN, protocol type 47 for GRE) and bind stripping actions. When traffic matches the rules, the VTEP hardware chip automatically strips the specified tunnel headers (VXLAN/UDP/IP outer headers, MPLS labels, etc.) and forwards the original Layer 2 payload.
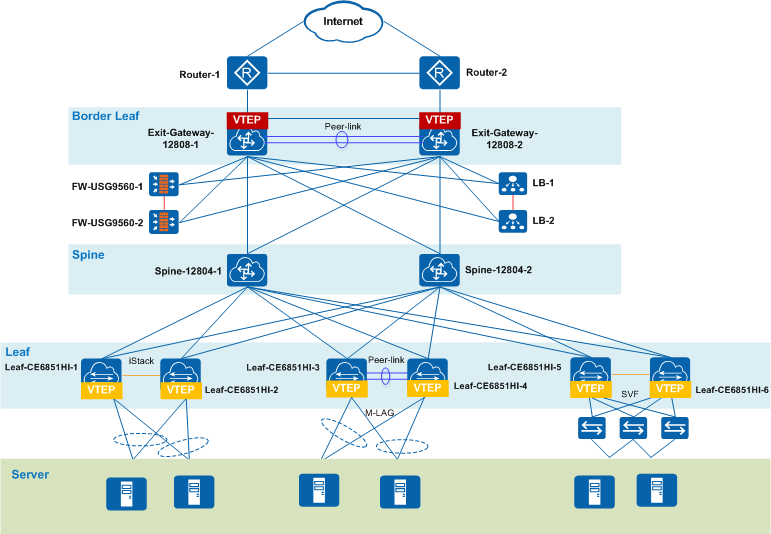
Distributed gateway synergy: In Spine-Leaf VXLAN architectures, physical VTEPs (Leaf nodes) can collaborate with Layer 3 gateways to complete multi-layer stripping. For example, after Spine nodes forward MPLS-encapsulated VXLAN traffic to Leaf VTEPs, the VTEPs first strip MPLS labels, then perform VXLAN decapsulation.
Do you need a configuration example for a specific vendor's VTEP device (such as Mylinking™ VXLAN-capable Network Packet Brokers) to implement tunnel encapsulation stripping?
Practical Application Scenario
Consider a large enterprise data center deploying a VXLAN overlay network with the switches(e.g. Mylinking™) as VTEPs, supporting multiple tenant VMs. The data center uses MPLS for traffic transmission between core switches and VXLAN for VM-to-VM communication. Additionally, remote branch offices send traffic to the data center via GRE tunnels. To ensure security and visibility, the enterprise deploys an NPB with Tunnel Encapsulation Stripping between the core network and the VTEPs.
When traffic arrives at the data center:
(1) The NPB first strips MPLS headers from traffic coming from the core network and GRE headers from branch office traffic.
(2) For VXLAN traffic between VTEPs, the NPB can strip outer VXLAN headers when forwarding traffic to monitoring tools, allowing the tools to inspect the original VM traffic.
(3) The NPB forwards the pre-processed (header-stripped) traffic to the VTEPs, which only need to handle VXLAN encapsulation/decapsulation for the native payload. This setup reduces VTEP processing load, enables comprehensive traffic analysis, and ensures seamless interoperability between MPLS, GRE, and VXLAN segments.
VTEPs are the backbone of VXLAN networks, enabling scalable virtualization and multi-tenant communication. However, the growing complexity of encapsulated traffic in modern networks poses significant challenges to VTEP performance and network visibility. Network Packet Brokers with Tunnel Encapsulation Stripping capabilities address these challenges by pre-processing traffic, stripping diverse headers (VXLAN, VLAN, GRE, GTP, MPLS, IPIP) before it reaches VTEPs or monitoring tools. This not only optimizes VTEP performance by reducing processing overhead but also enhances network visibility, strengthens security, and improves interoperability across heterogeneous environments.
As organizations continue to adopt cloud-native architectures and hybrid cloud deployments, the synergy between NPBs and VTEPs will become increasingly critical. By leveraging NPBs' tunnel encapsulation stripping function, network administrators can unlock the full potential of VXLAN networks, ensuring they are efficient, secure, and adaptable to evolving business needs.
Post time: Jan-09-2026