Driven by digital transformation, enterprise networks are no longer simply "a few cables connecting computers." With the proliferation of IoT devices, the migration of services to the cloud, and the increasing adoption of remote work, network traffic has exploded, like traffic on a highway. However, this surge in traffic also presents challenges: security tools can't capture critical data, monitoring systems are overwhelmed by redundant information, and threats hidden in encrypted traffic go undetected. This is where the "invisible butler" called a Network Packet Broker (NPB) comes in handy. Acting as an intelligent bridge between network traffic and monitoring tools, it handles the chaotic flow of traffic across the entire network while accurately feeding monitoring tools the data they need, helping enterprises solve the "invisible, inaccessible" network challenges. Today, we'll provide a comprehensive understanding of this core role in network operations and maintenance.
1. Why are companies looking for NPBs now? — The "Visibility Need" of Complex Networks
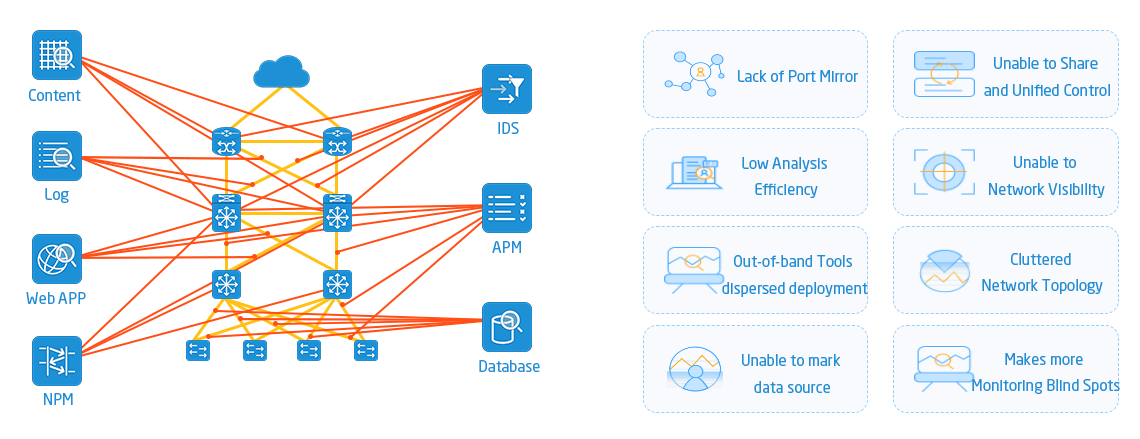
Consider this: When your network is running hundreds of IoT devices, hundreds of cloud servers, and employees accessing it remotely from all over the place, how can you ensure that no malicious traffic sneaks in? How can you determine which links are congested and slowing down business operations?
Traditional monitoring methods have long been inadequate: either monitoring tools can only focus on specific traffic segments, missing key nodes; or they pass all traffic to the tool at once, causing it to be unable to digest the information and slowing down analysis efficiency. Furthermore, with over 70% of traffic now encrypted, traditional tools are completely unable to see through its content.
The emergence of NPBs addresses the pain point of "lack of network visibility." They sit between traffic entry points and monitoring tools, aggregating dispersed traffic, filtering out redundant data, and ultimately distributing precise traffic to IDS (Intrusion Detection Systems), SIEMs (Security Information Management Platforms), performance analysis tools, and more. This ensures that monitoring tools are neither starved nor oversaturated. NPBs can also decrypt and encrypt traffic, protecting sensitive data and providing enterprises with a clear overview of their network status.
It can be said that now as long as an enterprise has network security, performance optimization or compliance needs, NPB has become an unavoidable core component.
What is NPB? — A Simple Analysis from Architecture to Core Capabilities
Many people think the term "packet broker" carries a high technical barrier to entry. However, a more accessible analogy is to use a "express delivery sorting center": network traffic is "express parcels," the NPB is the "sorting center," and the monitoring tool is the "receiving point." The NPB's job is to aggregate scattered parcels (aggregation), remove invalid parcels (filtering), and sort them by address (distribution). It can also unpack and inspect special parcels (decryption) and remove private information (massaging)—the entire process is efficient and precise.
1. First, let’s look at the “skeleton” of NPB: three core architectural modules
The NPB workflow relies entirely on the collaboration of these three modules; none of them can be missing:
○ Traffic Access Module: It is equivalent to the "express delivery port" and is specifically used to receive network traffic from the switch mirror port (SPAN) or splitter (TAP). Regardless of whether it is traffic from a physical link or a virtual network, it can be collected in a unified manner.
○ Processing Engine:This is the "core brain of the sorting center" and is responsible for the most critical "processing" - such as merging multi-link traffic (aggregation), filtering out traffic from a certain type of IP (filtering), copying the same traffic and sending it to different tools (copying), decrypting SSL/TLS encrypted traffic (decryption), etc. All "fine operations" are completed here.
○ Distribution Module: It is like a "courier" who accurately distributes the processed traffic to the corresponding monitoring tools and can also perform load balancing - for example, if a performance analysis tool is too busy, part of the traffic will be distributed to the backup tool to avoid overloading a single tool.
2. NPB's "Hard Core Capabilities": 12 core functions solve 90% of network problems
NPB has many functions, but let's focus on the most commonly used ones by enterprises. Each one corresponds to a practical pain point:
○ Traffic Replication / Aggregation + Filtering For example, if an enterprise has 10 network links, the NPB first merges the traffic of the 10 links, then filters out "duplicate data packets" and "irrelevant traffic" (such as traffic from employees watching videos), and only sends business-related traffic to the monitoring tool - directly improving efficiency by 300%.
○ SSL/TLS Decryption: Nowadays, many malicious attacks are hidden in HTTPS encrypted traffic. NPB can safely decrypt this traffic, allowing tools such as IDS and IPS to "see through" the encrypted content and capture hidden threats such as phishing links and malicious code.
○ Data Masking / Desensitization: If the traffic contains sensitive information such as credit card numbers and social security numbers, NPB will automatically "erase" this information before sending it to the monitoring tool. This will not affect the tool's analysis, but will also comply with PCI-DSS (payment compliance) and HIPAA (healthcare compliance) requirements to prevent data leakage.
○ Load Balancing + Failover If an enterprise has three SIEM tools, the NPB will evenly distribute traffic among them to prevent any one tool from being overwhelmed. If one tool fails, the NPB will immediately switch traffic to the backup tool to ensure uninterrupted monitoring. This is especially important for industries such as finance and healthcare where downtime is unacceptable.
○ Tunnel Termination: VXLAN, GRE and other "Tunnel Protocols" are now commonly used in cloud networks. Traditional tools cannot understand these protocols. NPB can "disassemble" these tunnels and extract the real traffic inside, allowing old tools to process traffic in cloud environments.
The combination of these features enables NPB to not only "see through" encrypted traffic, but also "protect" sensitive data and "adapt" to various complex network environments - this is why it can become a core component.
III. Where is NPB used? — Five key scenarios that address real enterprise needs
NPB isn't a one-size-fits-all tool; instead, it adapts flexibly to different scenarios. Whether it's a data center, a 5G network, or a cloud environment, it finds precise applications. Let's look at a few typical cases to illustrate this point:
1. Data Center: The Key to Monitoring East-West Traffic
Traditional data centers focus solely on north-south traffic (traffic from servers to the outside world). However, in virtualized data centers, 80% of traffic is east-west (traffic between virtual machines), which traditional tools simply cannot capture. This is where NPBs come in handy:
For example, a large internet company uses VMware to build a virtualized data center. The NPB is directly integrated with vSphere (VMware's management platform) to accurately capture east-west traffic between virtual machines and distribute it to IDS and performance tools. This not only eliminates "monitoring blind spots," but also increases tool efficiency by 40% through traffic filtering, directly cutting the data center's mean-time-to-repair (MTTR) in half.
In addition, NPB can monitor server load and ensure that payment data complies with PCI-DSS, becoming an "essential operation and maintenance requirement" for data centers.
2. SDN/NFV Environment: Flexible Roles Adapting to Software-Defined Networking
Many companies are now using SDN (Software Defined Networking) or NFV (Network Function Virtualization). Networks are no longer fixed hardware, but rather flexible software services. This requires NPBs to become more flexible:
For example, a university uses SDN to implement "Bring Your Own Device (BYOD)" so that students and teachers can connect to the campus network using their phones and computers. NPB is integrated with an SDN controller (such as OpenDaylight) to ensure traffic isolation between teaching and office areas while accurately distributing traffic from each area to monitoring tools. This approach does not affect students and teachers' use, and allows for timely detection of abnormal connections, such as access from malicious off-campus IP addresses.
The same is true for NFV environments. NPB can monitor the traffic of virtual firewalls (vFWs) and virtual load balancers (vLBs) to ensure the stable performance of these "software devices", which is much more flexible than traditional hardware monitoring.
3. 5G Networks: Managing Sliced Traffic and Edge Nodes
The core features of 5G are "high speed, low latency, and large connections", but this also brings new challenges to monitoring: for example, 5G's "network slicing" technology can divide the same physical network into multiple logical networks (for example, a low-latency slice for autonomous driving and a large-connection slice for IoT), and the traffic in each slice must be monitored independently.
One operator used NPB to solve this problem: it deployed independent NPB monitoring for each 5G slice, which can not only view the latency and throughput of each slice in real time, but also intercept abnormal traffic (such as unauthorized access between slices) in a timely manner, ensuring the low latency requirements of key businesses such as autonomous driving.
In addition, 5G edge computing nodes are scattered across the country, and NPB can also provide a "lightweight version" that is deployed at edge nodes to monitor distributed traffic and avoid delays caused by data transmission back and forth.
4. Cloud Environment/Hybrid IT: Breaking Down the Barriers of Public and Private Cloud Monitoring
Most enterprises now use a hybrid cloud architecture—some operations reside on Alibaba Cloud or Tencent Cloud (public clouds), some on their own private clouds, and some on local servers. In this scenario, traffic is dispersed across multiple environments, making monitoring easily interrupted.
China Minsheng Bank uses NPB to solve this pain point: its business uses Kubernetes for containerized deployment. NPB can directly capture traffic between containers (Pods) and correlate traffic between cloud servers and private clouds to form "end-to-end monitoring" - regardless of whether the business is in the public cloud or private cloud, as long as there is a performance problem, the operation and maintenance team can use NPB traffic data to quickly locate whether it is a problem with inter-container calls or cloud link congestion, improving diagnostic efficiency by 60%.
For multi-tenant public clouds, NPB can also ensure traffic isolation between different enterprises, prevent data leakage, and meet the compliance requirements of the financial industry.
In conclusion: NPB is not an “option” but a “must”
After reviewing these scenarios, you'll find that NPB is no longer a niche technology but a standard tool for enterprises to cope with complex networks. From data centers to 5G, from private clouds to hybrid IT, NPB can play a role wherever there's a need for network visibility.
With the increasing prevalence of AI and edge computing, network traffic will become even more complex, and NPB capabilities will be further upgraded (for example, using AI to automatically identify abnormal traffic and enabling more lightweight adaptation to edge nodes). For enterprises, understanding and deploying NPBs early will help them seize network initiative and avoid detours in their digital transformation.
Have you ever encountered network monitoring challenges in your industry? For example, can't see encrypted traffic, or hybrid cloud monitoring is interrupted? Feel free to share your thoughts in the comments section and let's explore solutions together.
Post time: Sep-23-2025