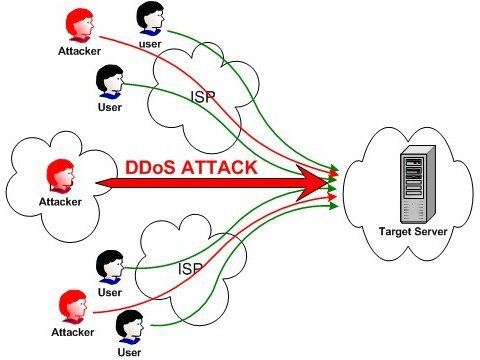
DDoS (Distributed Denial of Service) is a type of cyber attack where multiple compromised computers or devices are used to flood a target system or network with a massive volume of traffic, overwhelming its resources and causing a disruption in its normal functioning. The objective of a DDoS attack is to render the target system or network inaccessible to legitimate users.
Here are some key points about DDoS attacks:
1. Attack Method: DDoS attacks typically involve a large number of devices, known as a botnet, which are controlled by the attacker. These devices are often infected with malware that allows the attacker to remotely control and coordinate the attack.
2. Types of DDoS Attacks: DDoS attacks can take different forms, including volumetric attacks that flood the target with excessive traffic, application layer attacks that target specific applications or services, and protocol attacks that exploit vulnerabilities in network protocols.
3. Impact: DDoS attacks can have severe consequences, leading to service disruptions, downtime, financial losses, reputational damage, and compromised user experience. They can affect various entities, including websites, online services, e-commerce platforms, financial institutions, and even entire networks.
4. Mitigation: Organizations employ various DDoS mitigation techniques to protect their systems and networks. These include traffic filtering, rate limiting, anomaly detection, traffic diversion, and the use of specialized hardware or software solutions designed to identify and mitigate DDoS attacks.
5. Prevention: Preventing DDoS attacks requires a proactive approach that involves implementing robust network security measures, conducting regular vulnerability assessments, patching software vulnerabilities, and having incident response plans in place to handle attacks effectively.
It's important for organizations to stay vigilant and be prepared to respond to DDoS attacks, as they can have a significant impact on business operations and customer trust.
Defense Anti-DDoS attacks
1. Filter unnecessary services and ports
Inexpress, Express, Forwarding and other tools can be used to filter out unnecessary services and ports, that is to say, filter out fake ip on the router.
2. Cleaning and filtering of abnormal flow
Clean and filter abnormal traffic through the DDoS hardware firewall, and use top-level technologies such as data packet rule filtering, data flow fingerprint detection filtering, and data packet content customization filtering to accurately determine whether external access traffic is normal, and further prohibit filtering of abnormal traffic.
3. Distributed cluster defense
This is currently the most effective way to protect the cybersecurity community from massive DDoS attacks. If a node is attacked and cannot provide services, the system will automatically switch to another node according to the priority setting, and return all the attacker's data packets to the sending point, paralyzing the source of the attack and affecting the enterprise from a deeper security protection perspective security implementation decisions.
4. High security intelligent DNS analysis
The perfect combination of intelligent DNS resolution system and DDoS defense system provides enterprises with super detection capabilities for emerging security threats. At the same time, there is also a shutdown detection function, which can disable the server IP intelligence at any time to replace the normal server IP, so that the enterprise network can maintain a never-stop service state.
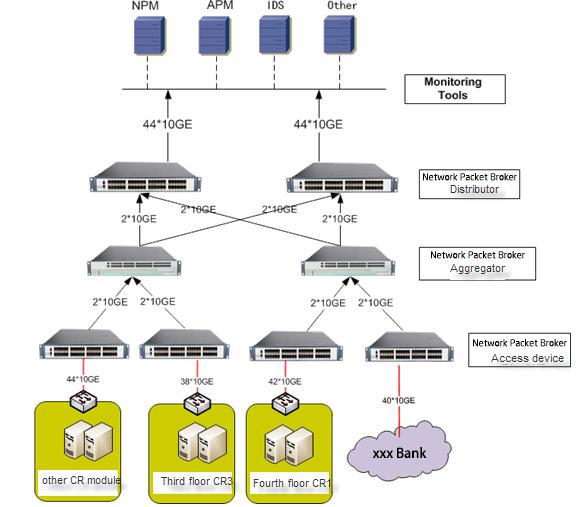
Anti DDoS Attacks for Bank Financial Network Security Traffic Managing, Detection & Cleaning:
1. Nanosecond response, fast and accurate.Business model traffic self-learning and packet by packet depth detection technology are adopted. Once abnormal traffic and message are found, the immediate protection strategy is launched to ensure that the delay between attack and defense is less than 2 seconds. At the same time, the abnormal flow cleaning solution based on layers of filter cleaning train of thought, through the seven layers of flow analysis processing, from IP reputation, the transport layer and application layer, feature recognition, session in seven aspects, the network behavior, the traffic shaping to prevent identification filtering step by step, improve the overall performance of the defense, effective guarantee of the XXX bank data center network security.
2. Separation of inspection and control, efficient and reliable. The separate deployment scheme of the test center and the cleaning center can ensure that the test center can continue to work after the failure of the cleaning center, and generate the test report and alarm notification in real time, which can show the attack of XXX bank to a large extent.
3. Flexible management, expansion worry-free.Anti-ddos solution can choose three management modes: detection without cleaning, automatic detection and cleaning protection, and manual interactive protection.The flexible use of the three management methods can meet the business requirements of XXX bank to reduce the implementation risk and improve the availability when the new business is launched.
Customer Value
1. Make effective use of network bandwidth to improve enterprise benefits
Through the overall security solution, the network security accident caused by DDoS attack on the online business of its data center was 0, and the waste of network outlet bandwidth caused by invalid traffic and the consumption of server resources were reduced, which created conditions for XXX bank to improve its benefits.
2. Reduce Risks, ensure network stability and business sustainability
The bypass deployment of anti-ddos equipment does not change the existing network architecture, no risk of network cutover, no single point of failure, no impact on the normal operation of the business, and reduces the implementation cost and operating cost.
3. Improve user satisfaction, consolidate existing users and develop new users
Provide users with a real network environment, online banking, online business inquiries and other online business user satisfaction has been greatly improved, consolidate user loyalty, to provide customers with real services.
Post time: Jul-17-2023