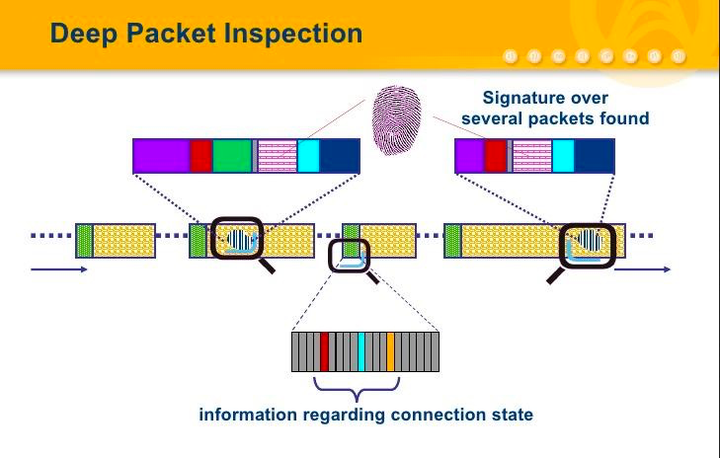
Deep Packet Inspection (DPI) is a technology used in Network Packet Brokers (NPBs) to inspect and analyze the contents of network packets at a granular level. It involves examining the payload, headers, and other protocol-specific information within packets to gain detailed insights into network traffic.
DPI goes beyond simple header analysis and provides a deep understanding of the data flowing through a network. It allows for in-depth inspection of the application layer protocols, such as HTTP, FTP, SMTP, VoIP, or video streaming protocols. By examining the actual content within packets, DPI can detect and identify specific applications, protocols, or even specific data patterns.
In addition to the hierarchical analysis of source addresses, destination addresses, source ports, destination ports, and protocol types, DPI also adds application-layer analysis to identify various applications and their contents. When the 1P packet, TCP or UDP data flow through the bandwidth management system based on DPI technology, the system reads the content of the 1P packet load to reorganize the application layer information in the OSI Layer 7 protocol, so as to get the content of the entire application program, and then shaping the traffic according to the management policy defined by the system.
How does DPI work?
Traditional firewalls often lack the processing power to perform thorough real-time checks on large volumes of traffic. As technology advances, DPI can be used to perform more complex checks to check headers and data. Typically, firewalls with intrusion detection systems often use DPI. In a world where digital information is Paramount, every piece of digital information is delivered over the Internet in small packets. This includes email, messages sent through the app, websites visited, video conversations, and more. In addition to the actual data, these packets include metadata that identifies the traffic source, content, destination, and other important information. With packet filtering technology, data can be continuously monitored and managed to ensure it is forwarded to the right place. But to ensure network security, traditional packet filtering is far from enough. Some of the main methods of deep packet inspection in network management are listed below:
Matching Mode/Signature
Each packet is checked for a match against a database of known network attacks by a firewall with intrusion detection system (IDS) capabilities. IDS searches for known malicious specific patterns and disables traffic when malicious patterns are found. The disadvantage of the signature matching policy is that it only applies to signatures that are updated frequently. In addition, this technology can only defend against known threats or attacks.
Protocol Exception
Since the protocol exception technique does not simply allow all data that does not match the signature database, the protocol exception technique used by the IDS firewall does not have the inherent flaws of the pattern/signature matching method. Instead, it adopts the default rejection policy. By protocol definition, firewalls decide what traffic should be allowed and protect the network from unknown threats.
Intrusion Prevention System (IPS)
IPS solutions can block the transmission of harmful packets based on their content, thereby stopping suspected attacks in real time. This means that if a packet represents a known security risk, IPS will proactively block network traffic based on a defined set of rules. One disadvantage of IPS is the need to regularly update a cyber threat database with details about new threats, and the possibility of false positives. But this danger can be mitigated by creating conservative policies and custom thresholds, establishing appropriate baseline behavior for network components, and periodically evaluating warnings and reported events to enhance monitoring and alerting.
1- The DPI (Deep Packet Inspection) in Network Packet Broker
The "deep" is level and ordinary packet analysis comparison, "ordinary packet inspection" only the following analysis of IP packet 4 layer, including the source address, destination address, source port, destination port and protocol type, and DPI except with the hierarchical analysis, also increased the application layer analysis, identify the various applications and content, to realize the main functions:
1) Application Analysis -- network traffic composition analysis, performance analysis, and flow analysis
2) User Analysis -- user group differentiation, behavior analysis, terminal analysis, trend analysis, etc.
3) Network Element Analysis -- analysis based on regional attributes (city, district, street, etc.) and base station load
4) Traffic Control -- P2P speed limiting, QoS assurance, bandwidth assurance, network resource optimization, etc.
5) Security Assurance -- DDoS attacks, data broadcast storm, prevention of malicious virus attacks, etc.
2- General Classification of Network Applications
Today there are countless applications on the Internet, but the common web applications can be exhaustive.
As far as I know, the best app recognition company is Huawei, which claims to recognize 4,000 apps. Protocol analysis is the basic module of many firewall companies (Huawei, ZTE, etc.), and it is also a very important module, supporting the realization of other functional modules, accurate application identification, and greatly improving the performance and reliability of products. In modeling malware identification based on network traffic characteristics, as I am doing now, accurate and extensive protocol identification is also very important. Excluding the network traffic of common applications from the company's export traffic, the remaining traffic will account for a small proportion, which is better for malware analysis and alarm.
Based on my experience, the existing commonly used applications are classified according to their functions:
PS: According to personal understanding of the application classification, you have any good suggestions welcome to leave a message proposal
1). E-mail
2). Video
3). Games
4). Office OA class
5). Software update
6). Financial (bank, Alipay)
7). Stocks
8). Social Communication (IM software)
9). Web browsing (probably better identified with URLs)
10). Download tools (web disk, P2P download, BT related)
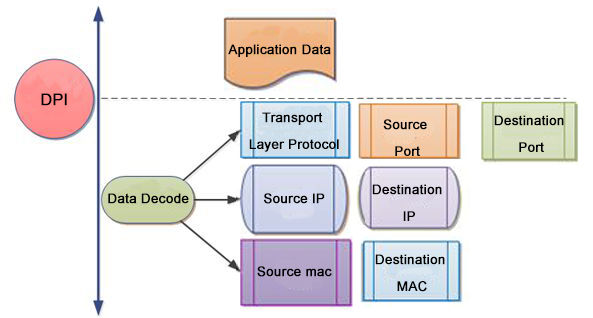
Then, how DPI(Deep Packet Inspection) works in an NPB:
1). Packet Capture: The NPB captures network traffic from various sources, such as switches, routers, or taps. It receives packets flowing through the network.
2). Packet Parsing: The captured packets are parsed by the NPB to extract various protocol layers and associated data. This parsing process helps identify the different components within the packets, such as Ethernet headers, IP headers, transport layer headers (e.g., TCP or UDP), and application layer protocols.
3). Payload Analysis: With DPI, the NPB goes beyond header inspection and focuses on the payload, including the actual data within the packets. It examines the payload content in-depth, irrespective of the application or protocol used, to extract relevant information.
4). Protocol Identification: DPI enables the NPB to identify the specific protocols and applications being used within the network traffic. It can detect and classify protocols like HTTP, FTP, SMTP, DNS, VoIP, or video streaming protocols.
5). Content Inspection: DPI allows the NPB to inspect the content of packets for specific patterns, signatures, or keywords. This enables the detection of network threats, such as malware, viruses, intrusion attempts, or suspicious activities. DPI can also be used for content filtering, enforcing network policies, or identifying data compliance violations.
6). Metadata Extraction: During DPI, the NPB extracts relevant metadata from the packets. This can include information such as source and destination IP addresses, port numbers, session details, transaction data, or any other relevant attributes.
7). Traffic Routing or Filtering: Based on the DPI analysis, the NPB can route specific packets to designated destinations for further processing, such as security appliances, monitoring tools, or analytics platforms. It can also apply filtering rules to discard or redirect packets based on the identified content or patterns.
Post time: Jun-25-2023